| Q:1 | What are the differences between Get and post methods in form submitting. give the case where we can use get and we can use post methods? |
||||||||||||||||||||
| A:1 | When to use GET or POST
The HTML 2.0 specification says, in section Form
Submission (and the HTML 4.0 specification repeats this with minor stylistic changes):
–>If the processing of a form is idempotent
(i.e. it has no lasting observable effect on the state of the world), then the form method should be GET. Many database searches have no visible side-effects and make ideal applications of query forms. – –>If the service associated with the processing of a form has side effects (for example, modification of a database or subscription to a service), the method should be POST. How the form data is transmitted?
quotation from the HTML 4.0 specification
–> If the method is “get” – -, the user agent
takes the value of action, appends a ? to it, then appends the form data set, encoded using the application/x-www-form-urlencoded content type. The user agent then traverses the link to this URI. In this scenario, form data are restricted to ASCII codes. –> If the method is “post” –, the user agent conducts an HTTP post transaction using the value of the action attribute and a message created according to the content type specified by the enctype attribute. |
||||||||||||||||||||
| Q:2 | Who is the father of PHP and explain the changes in PHP versions? |
||||||||||||||||||||
| A:2 | Rasmus Lerdorf is known as the father of PHP.PHP/FI 2.0 is an early and no longer supported version of PHP. PHP 3 is the successor to PHP/FI 2.0 and is a lot nicer. PHP 4 is the current generation of PHP, which uses the Zend engine under the hood. PHP 5 uses Zend engine 2 which, among other things, offers many additionalOOP features |
||||||||||||||||||||
| Q:3 | How can we submit a form without a submit button? | ||||||||||||||||||||
| A:3 | The main idea behind this is to use Java script submit() function in order to submit the form without explicitly clicking any submit button. You can attach the document.formname.submit() method to onclick, onchange events of different inputs and perform the form submission. you can even built a timer function where you can automatically submit the form after xx seconds once the loading is done (can be seen in online test sites). |
||||||||||||||||||||
| Q:4 | In how many ways we can retrieve the data in the result set of MySQL using PHP? |
||||||||||||||||||||
| A:4 | You can do it by 4 Ways1. mysql_fetch_row. 2. mysql_fetch_array 3. mysql_fetch_object 4. mysql_fetch_assoc |
||||||||||||||||||||
| Q:5 | What is the difference between mysql_fetch_object and mysql_fetch_array? |
||||||||||||||||||||
| A:5 | mysql_fetch_object() is similar tomysql_fetch_array(), with one difference - an object is returned, instead of an array. Indirectly, that means that you can only access the data by the field names, and not by their offsets (numbers are illegal property names). |
||||||||||||||||||||
| Q:6 | What is the difference between $message and $$message? | ||||||||||||||||||||
| A:6 | It is a classic example of PHP’s variable variables. take the following example.$message = “Mizan”;$$message = “is a moderator of PHPXperts.”;$message is a simple PHP variable that we are used to. But the $$message is not a very familiar face. It creates a variable name $mizan with the value “is a moderator of PHPXperts.” assigned. break it like this${$message} => $mizanSometimes it is convenient to be able to have variable variable names. That is, a variable name which can be set and used dynamically. |
||||||||||||||||||||
| Q:7 | How can we extract string ‘abc.com ‘ from a string ‘http://info@abc.com’ using regular expression of PHP? |
||||||||||||||||||||
| A:7 | preg_match(“/^http:\/\/.+@(.+)$/”,’http://info@abc.com’,$found); echo $found[1]; |
||||||||||||||||||||
| Q:8 | How can we create a database using PHP and MySQL? | ||||||||||||||||||||
| A:8 | We can create MySQL database with the use of mysql_create_db(“Database Name”) |
||||||||||||||||||||
| Q:9 | What are the differences between require and include, include_once and require_once? |
||||||||||||||||||||
| A:9 | The include() statement includes and evaluates the specified file.The documentation below also applies to require(). The two constructs are identical in every way except how they handle failure. include() produces a Warning while require() results in a Fatal Error. In other words, use require() if you want a missing file to halt processing of the page. include() does not behave this way, the script will continue regardless. The include_once() statement includes and evaluates the specified file during the execution of the script. This is a behavior similar to the include() statement, with the only difference being that if the code from a file has already been included, it will not be included again. As the name suggests, it will be included just once.include_once() should be used in cases where the same file might be included and evaluated more than once during a particular execution of a script, and you want to be sure that it is included exactly once to avoid problems with function redefinitions, variable value reassignments, etc. require_once() should be used in cases where the same file might be included and evaluated more than once during a particular execution of a script, and you want to be sure that it is included exactly once to avoid problems with function redefinitions, variable value reassignments, etc. |
||||||||||||||||||||
| Q:10 | Can we use include (”abc.PHP”) two times in a PHP page “makeit.PHP”? |
||||||||||||||||||||
| A:10 | Yes we can use include() more than one time in any page though it is not a very good practice. |
||||||||||||||||||||
| Q:11 | What are the different tables present in MySQL, which type of table is generated when we are creating a table in the following syntax: create table employee (eno int(2),ename varchar(10)) ? |
||||||||||||||||||||
| A:11 | Total 5 types of tables we can create 1. MyISAM 2. Heap 3. Merge 4. INNO DB 5. ISAM MyISAM is the default storage engine as of MySQL 3.23 and as a result if we do not specify the table name explicitly it will be assigned to the default engine. |
||||||||||||||||||||
| Q:12 | Functions in IMAP, POP3 AND LDAP? | ||||||||||||||||||||
| A:12 | You can find these specific information in PHP Manual. | ||||||||||||||||||||
| Q:13 | How can I execute a PHP script using command line? | ||||||||||||||||||||
| A:13 | As of version 4.3.0, PHP supports a new SAPI type (Server Application Programming Interface) named CLI which means Command Line Interface. Just run the PHP CLI (Command Line Interface) program and provide the PHP script file name as the command line argument. For example, “php myScript.php”, assuming “php” is the command to invoke the CLI program. Be aware that if your PHP script was written for the Web CGI interface, it may not execute properly in command line environment. |
||||||||||||||||||||
| Q:14 | Suppose your Zend engine supports the mode <? ?> Then how can u configure your PHP Zend engine to support <?PHP ?> mode ? |
||||||||||||||||||||
| A:14 | In php.ini file: set short_open_tag=on to make PHP support |
||||||||||||||||||||
| Q:15 | Shopping cart online validation i.e. how can we configure Paypal, etc.? |
||||||||||||||||||||
| A:15 | We can find the detail documentation about different paypal integration process at the following site
|
||||||||||||||||||||
| Q:16 | What is meant by nl2br()? | ||||||||||||||||||||
| A:16 | Inserts HTML line breaks (<BR />) before all newlines in a string string nl2br (string); Returns string with ” inserted before all newlines. For example: echo nl2br(“god bless\n you”) will output “god bless <br /> you” to your browser. |
||||||||||||||||||||
| Q:17 | Draw the architecture of Zend engine? | ||||||||||||||||||||
| A:17 | The Zend Engine is the internal compiler and runtime engine used by PHP4. Developed by Zeev Suraski and Andi Gutmans, the Zend Engine is an abbreviation of their names. In the early days of PHP4, it worked as follows: 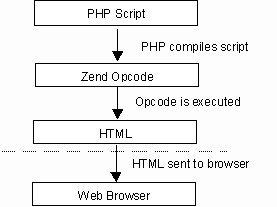 The PHP script was loaded by the Zend Engine and compiled into Zend The PHP script was loaded by the Zend Engine and compiled into Zendopcode. Opcodes, short for operation codes, are low level binary instructions. Then the opcode was executed and the HTML generated sent to the client. The opcode was flushed from memory after execution.Today, there are a multitude of products and techniques to help you speed up this process. In the following diagram, we show the how modern PHP scripts work; all the shaded boxes are optional. 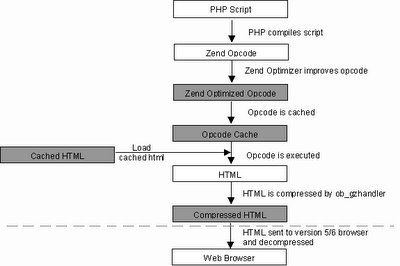 PHP Scripts are loaded into memory and compiled into Zend opcodes. PHP Scripts are loaded into memory and compiled into Zend opcodes. |
||||||||||||||||||||
| Q:18 | What are the current versions of apache, PHP, and MySQL? | ||||||||||||||||||||
| A:18 | As of February, 2007 the current versions arePHP: php5.2.1 MySQL: MySQL 5.2 Apache: Apache 2.2.4Note: visit www.php.net, http://dev.mysql.com/downloads/mysql/, www.apache.org to get current versions. |
||||||||||||||||||||
| Q:19 | What are the reasons for selecting lamp (Linux, apache, MySQL, PHP) instead of combination of other software programs, servers and operating systems? |
||||||||||||||||||||
| A:19 | All of those are open source resource. Security of Linux is very very more than windows. Apache is a better server that IIS both in functionality and security. MySQL is world most popular open source database. PHP is more faster that asp or any other scripting language. |
||||||||||||||||||||
| Q:20 | How can we encrypt and decrypt a data present in a MySQL table using MySQL? |
||||||||||||||||||||
| A:20 | AES_ENCRYPT () and AES_DECRYPT () | ||||||||||||||||||||
| Q:21 | How can we encrypt the username and password using PHP? | ||||||||||||||||||||
| A:21 | The functions in this section perform encryption and decryption, and compression and uncompression:
|
||||||||||||||||||||
| Q:22 | What are the features and advantages of object-oriented programming? |
||||||||||||||||||||
| A:22 | One of the main advantages of OO programming is its ease of modification; objects can easily be modified and added to a system there by reducing maintenance costs. OO programming is also considered to be better at modeling the real world than is procedural programming. It allows for more complicated and flexible interactions. OO systems are also easier for non-technical personnel to understand and easier for them to participate in the maintenance and enhancement of a system because it appeals to natural human cognition patterns. For some systems, an OO approach can speed development time since many objects are standard across systems and can be reused. Components that manage dates, shipping, shopping carts, etc. can be purchased and easily modified for a specific system |
||||||||||||||||||||
| Q:23 | What are the differences between procedure-oriented languages and object-oriented languages? |
||||||||||||||||||||
| A:23 | Traditional programming has the following characteristics:Functions are written sequentially, so that a change in programming can affect any code that follows it. If a function is used multiple times in a system (i.e., a piece of code that manages the date), it is often simply cut and pasted into each program (i.e., a change log, order function, fulfillment system, etc). If a date change is needed (i.e., Y2K when the code needed to be changed to handle four numerical digits instead of two), all these pieces of code must be found, modified, and tested. Code (sequences of computer instructions) and data (information on which the instructions operates on) are kept separate. Multiple sets of code can access and modify one set of data. One set of code may rely on data in multiple places. Multiple sets of code and data are required to work together. Changes made to any of the code sets and data sets can cause problems through out the system.Object-Oriented programming takes a radically different approach:Code and data are merged into one indivisible item – an object (the term “component” has also been used to describe an object.) An object is an abstraction of a set of real-world things (for example, an object may be created around “date”) The object would contain all information and functionality for that thing (A date object it may contain labels like January, February, Tuesday, Wednesday. It may contain functionality that manages leap years, determines if it is a business day or a holiday, etc., See Fig. 1). Ideally, information about a particular thing should reside in only one place in a system. The information within an object is encapsulated (or hidden) from the rest of the system. A system is composed of multiple objects (i.e., date function, reports, order processing, etc., See Fig 2). When one object needs information from another object, a request is sent asking for specific information. (for example, a report object may need to know what today’s date is and will send a request to the date object) These requests are called messages and each object has an interface that manages messages. OO programming languages include features such as “class”, “instance”, “inheritance”, and “polymorphism” that increase the power and flexibility of an object. |
||||||||||||||||||||
| Q:24 | What is the use of friend function? | ||||||||||||||||||||
| A:24 | Sometimes a function is best shared among a number of different classes. Such functions can be declared either as member functions of one class or as global functions. In either case they can be set to be friends of other classes, by using a friend specifier in the class that is admitting them. Such functions can use all attributes of the class which names them as a friend, as if they were themselves members of that class. A friend declaration is essentially a prototype for a member function, but instead of requiring an implementation with the name of that class attached by the double colon syntax, a global function or member function of another class provides the match. |
||||||||||||||||||||
| Q:25 | What are the differences between public, private, protected, static, transient, final and volatile? |
||||||||||||||||||||
| A:25 | Public: Public declared items can be accessed everywhere. Protected: Protected limits access to inherited and parent classes (and to the class that defines the item). Private: Private limits visibility only to the class that defines the item. Static: A static variable exists only in a local function scope, but it does not lose its value when program execution leaves this scope. Final: Final keyword prevents child classes from overriding a method by prefixing the definition with final. If the class itself is being defined final then it cannot be extended. transient: A transient variable is a variable that may not be serialized. volatile: a variable that might be concurrently modified by multiple threads should be declared volatile. Variables declared to be volatile will not be optimized by the compiler because their value can change at any time. |
||||||||||||||||||||
| Q:26 | What are the different types of errors in PHP? | ||||||||||||||||||||
| A:26 | Three are three types of errors:1. Notices: These are trivial, non-critical errors that PHP encounters while executing a script – for example, accessing a variable that has not yet been defined. By default, such errors are not displayed to the user at all – although, as you will see, you can change this default behavior.2. Warnings: These are more serious errors – for example, attempting to include() a file which does not exist. By default, these errors are displayed to the user, but they do not result in script termination.3. Fatal errors: These are critical errors – for example, instantiating an object of a non-existent class, or calling a non-existent function. These errors cause the immediate termination of the script, and PHP’s default behavior is to display them to the user when they take place. |
||||||||||||||||||||
| Q:27 | What is the functionality of the function strstr and stristr? | ||||||||||||||||||||
| A:27 | strstr:
Returns part of haystack string from the first occurrence of needle to the end of haystack.If needle is not found, returns FALSE. If needle is not a string, it is converted to an integer and applied as the ordinal value of a character. This function is case-sensitive. For case-insensitive searches, use stristr(). |
||||||||||||||||||||
| Q:28 | What are the differences between PHP 3 and PHP 4 and PHP 5? | ||||||||||||||||||||
| A:28 | Please read the release notes at http://www.php.net. |
||||||||||||||||||||
| Q:29 | How can we convert asp pages to PHP pages? | ||||||||||||||||||||
| A:29 | there are lots of tools available for asp to PHP conversion. you can search Google for that. the best one is available athttp://asp2php.naken.cc./ |
||||||||||||||||||||
| Q:30 | What is the functionality of the function htmlentities? | ||||||||||||||||||||
| A:30 | Convert all applicable characters to HTML entities This function is identical to htmlspecialchars() in all ways, except with htmlentities(), all characters which have HTML character entity equivalents are translated into these entities. |
||||||||||||||||||||
| Q:31 | How can we get second of the current time using date function? |
||||||||||||||||||||
| A:31 | $second = date(“s”); | ||||||||||||||||||||
| Q:32 | How can we convert the time zones using PHP? | ||||||||||||||||||||
| A:32 | By using date_default_timezone_get and date_default_timezone_set function on PHP 5.1.0 <?php // Discover what 8am in Tokyo relates to on the East Coast of the US // Set the default timezone to Tokyo time: date_default_timezone_set('Asia/Tokyo'); // Now generate the timestamp for that particular timezone, on Jan 1st, 2000 $stamp = mktime(8, 0, 0, 1, 1, 2000); // Now set the timezone back to US/Eastern date_default_timezone_set('US/Eastern'); // Output the date in a standard format (RFC1123), this will print: // Fri, 31 Dec 1999 18:00:00 EST echo '<p>', date(DATE_RFC1123, $stamp) ,'</p>';?>
|
||||||||||||||||||||
| Q:33 | What is meant by urlencode and urldocode? | ||||||||||||||||||||
| A:33 | URLencode returns a string in which all non-alphanumeric characters except -_. have been replaced with a percent (%) sign followed by two hex digits and spaces encoded as plus (+) signs. It is encoded the same way that the posted data from a WWW form is encoded, that is the same way as in application/x-www-form-urlencoded media type. urldecode decodes any %## encoding in the given string. |
||||||||||||||||||||
| Q:34 | What is the difference between the functions unlink and unset? |
||||||||||||||||||||
| A:34 | unlink() deletes the given file from the file system. unset() makes a variable undefined. |
||||||||||||||||||||
| Q:35 | How can we register the variables into a session? | ||||||||||||||||||||
| A:35 | $_SESSION[’name’] = “Mizan”; | ||||||||||||||||||||
| Q:36 | How can we get the properties (size, type, width, height) of an image using PHP image functions? |
||||||||||||||||||||
| A:36 | To know the Image type use exif_imagetype () function To know the Image size use getimagesize () function To know the image width use imagesx () function To know the image height use imagesy() function t |
||||||||||||||||||||
| Q:37 | How can we get the browser properties using PHP? | ||||||||||||||||||||
| A:37 | By using $_SERVER['HTTP_USER_AGENT'] variable. |
||||||||||||||||||||
| Q:38 | What is the maximum size of a file that can be uploaded using PHP and how can we change this? |
||||||||||||||||||||
| A:38 | By default the maximum size is 2MB. and we can change the following setup at php.iniupload_max_filesize = 2M |
||||||||||||||||||||
| Q:39 | How can we increase the execution time of a PHP script? | ||||||||||||||||||||
| A:39 | by changing the following setup at php.inimax_execution_time = 30 ; Maximum execution time of each script, in seconds |
||||||||||||||||||||
| Q:40 | How can we take a backup of a MySQL table and how can we restore it. ? |
||||||||||||||||||||
| A:40 | To backup: BACKUP TABLE tbl_name[,tbl_name…] TO ‘/path/to/backup/directory’ RESTORE TABLE tbl_name[,tbl_name…] FROM ‘/path/to/backup/directory’mysqldump: Dumping Table Structure and DataUtility to dump a database or a collection of database for backup or for transferring the data to another SQL server (not necessarily a MySQL server). The dump will contain SQL statements to create the table and/or populate the table. -t, –no-create-info Don’t write table creation information (the CREATE TABLE statement). -d, –no-data Don’t write any row information for the table. This is very useful if you just want to get a dump of the structure for a table! |
||||||||||||||||||||
| Q:41 | How can we optimize or increase the speed of a MySQL select query? |
||||||||||||||||||||
| A:41 |
|
||||||||||||||||||||
| Q:42 | How many ways can we get the value of current session id? | ||||||||||||||||||||
| A:42 | session_id() returns the session id for the current session. | ||||||||||||||||||||
| Q:43 | How can we destroy the session, how can we unset the variable of a session? |
||||||||||||||||||||
| A:43 | session_unregister — Unregister a global variable from the current session session_unset — Free all session variables |
||||||||||||||||||||
| Q:44 | How can we destroy the cookie? | ||||||||||||||||||||
| A:44 | Set the cookie in past. | ||||||||||||||||||||
| Q:45 | How many ways we can pass the variable through the navigation between the pages? |
||||||||||||||||||||
| A:45 |
|
||||||||||||||||||||
| Q:46 | What is the difference between ereg_replace() and eregi_replace()? |
||||||||||||||||||||
| A:46 | eregi_replace() function is identical to ereg_replace() except that this ignores case distinction when matching alphabetic characters.eregi_replace() function is identical to ereg_replace() except that this ignores case distinction when matching alphabetic characters. |
||||||||||||||||||||
| Q:47 | What are the different functions in sorting an array? | ||||||||||||||||||||
| A:47 | Sort(), arsort(), asort(), ksort(), natsort(), natcasesort(), rsort(), usort(), array_multisort(), and uksort(). |
||||||||||||||||||||
| Q:48 | How can we know the count/number of elements of an array? | ||||||||||||||||||||
| A:48 | 2 ways a) sizeof($urarray) This function is an alias of count() b) count($urarray) |
||||||||||||||||||||
| Q:49 | What is the PHP predefined variable that tells the What types of images that PHP supports? |
||||||||||||||||||||
| A:49 | Though i am not sure if this is wrong or not, With the exif extension you are able to work with image meta data. |
||||||||||||||||||||
| Q:50 | How can I know that a variable is a number or not using a JavaScript? |
||||||||||||||||||||
| A:50 | bool is_numeric ( mixed var) Returns TRUE if var is a number or a numeric string, FALSE otherwise.or use isNaN(mixed var)The isNaN() function is used to check if a value is not a number. |
||||||||||||||||||||
| Q:51 | List out some tools through which we can draw E-R diagrams for mysql. |
||||||||||||||||||||
| A:51 | Case Studio Smart Draw |
||||||||||||||||||||
| Q:52 | How can I retrieve values from one database server and store them in other database server using PHP? |
||||||||||||||||||||
| A:52 | we can always fetch from one database and rewrite to another. here is a nice solution of it.$db1 = mysql_connect(“host”,”user”,”pwd”) mysql_select_db(“db1″, $db1); $res1 = mysql_query(“query”,$db1);$db2 = mysql_connect(“host”,”user”,”pwd”) mysql_select_db(“db2″, $db2); $res2 = mysql_query(“query”,$db2);At this point you can only fetch records from you previous ResultSet, i.e $res1 – But you cannot execute new query in $db1, even if you supply the link as because the link was overwritten by the new db.so at this point the following script will fail $res3 = mysql_query(“query”,$db1); //this will failSo how to solve that? take a look below. $db1 = mysql_connect(“host”,”user”,”pwd”) mysql_select_db(“db1″, $db1); $res1 = mysql_query(“query”,$db1); $db2 = mysql_connect(“host”,”user”,”pwd”, true) mysql_select_db(“db2″, $db2); $res2 = mysql_query(“query”,$db2); So mysql_connect has another optional boolean parameter which indicates whether a link will be created or not. as we connect to the $db2 with this optional parameter set to ‘true’, so both link will remain live. now the following query will execute successfully. $res3 = mysql_query(“query”,$db1); Thanks goes to Hasan and Hasin for this solution. |
||||||||||||||||||||
| Q:53 | List out the predefined classes in PHP? | ||||||||||||||||||||
| A:53 | Directory stdClass __PHP_Incomplete_Class exception php_user_filter |
||||||||||||||||||||
| Q:54 | How can I make a script that can be bi-language (supports English, German)? |
||||||||||||||||||||
| A:54 | You can maintain two separate language file for each of the language. all the labels are putted in both language files as variables and assign those variables in the PHP source. on runtime choose the required language option. |
||||||||||||||||||||
| Q:55 | What are the difference between abstract class and interface? | ||||||||||||||||||||
| A:55 | Abstract class: abstract classes are the class where one or more methods are abstract but not necessarily all method has to be abstract. Abstract methods are the methods, which are declare in its class but not define. The definition of those methods must be in its extending class.Interface: Interfaces are one type of class where all the methods are abstract. That means all the methods only declared but not defined. All the methods must be define by its implemented class. |
||||||||||||||||||||
| Q:56 | How can we send mail using JavaScript? | ||||||||||||||||||||
| A:56 | JavaScript does not have any networking capabilities as it is designed to work on client site. As a result we can not send mails using JavaScript. But we can call the client side mail protocol mailto via JavaScript to prompt for an email to send. this requires the client to approve it. |
||||||||||||||||||||
| Q:57 | How can we repair a MySQL table? | ||||||||||||||||||||
| A:57 | The syntex for repairing a MySQL table is REPAIR TABLENAME, [TABLENAME, ], [Quick],[Extended] This command will repair the table specified if the quick is given the MySQL will do a repair of only the index tree if the extended is given it will create index row by row |
||||||||||||||||||||
| Q:58 | What are the advantages of stored procedures, triggers, indexes? |
||||||||||||||||||||
| A:58 | A stored procedure is a set of SQL commands that can be compiled and stored in the server. Once this has been done, clients don’t need to keep re-issuing the entire query but can refer to the stored procedure. This provides better overall performance because the query has to be parsed only once, and less information needs to be sent between the server and the client. You can also raise the conceptual level by having libraries of functions in the server. However, stored procedures of course do increase the load on the database server system, as more of the work is done on the server side and less on the client (application) side.Triggers will also be implemented. A trigger is effectively a type of stored procedure, one that is invoked when a particular event occurs. For example, you can install a stored procedure that is triggered each time a record is deleted from a transaction table and that stored procedure automatically deletes the corresponding customer from a customer table when all his transactions are deleted.Indexes are used to find rows with specific column values quickly. Without an index, MySQL must begin with the first row and then read through the entire table to find the relevant rows. The larger the table, the more this costs. If the table has an index for the columns in question, MySQL can quickly determine the position to seek to in the middle of the data file without having to look at all the data. If a table has 1,000 rows, this is at least 100 times faster than reading sequentially. If you need to access most of the rows, it is faster to read sequentially, because this minimizes disk seeks. |
||||||||||||||||||||
| Q:59 | What is the maximum length of a table name, database name, and fieldname in MySQL? |
||||||||||||||||||||
| A:59 | The following table describes the maximum length for each type of identifier.
identifiers: |
||||||||||||||||||||
| Q:60 | How many values can the SET function of MySQL take? | ||||||||||||||||||||
| A:60 | MySQL set can take zero or more values but at the maximum it can take 64 values |
||||||||||||||||||||
| Q:61 | What are the other commands to know the structure of table using MySQL commands except explain command? |
||||||||||||||||||||
| A:61 | describe Table-Name; | ||||||||||||||||||||
| Q:62 | How many tables will create when we create table, what are they? |
||||||||||||||||||||
| A:62 | The ‘.frm’ file stores the table definition. The data file has a ‘.MYD’ (MYData) extension. The index file has a ‘.MYI’ (MYIndex) extension, |
||||||||||||||||||||
| Q:63 | What is the purpose of the following files having extensions 1) .frm 2) .myd 3) .myi? What do these files contain? |
||||||||||||||||||||
| A:63 | In MySql, the default table type is MyISAM. Each MyISAM table is stored on disk in three files. The files have names that begin with the table name and have an extension to indicate the file type. The ‘.frm’ file stores the table definition. The data file has a ‘.MYD’ (MYData) extension. The index file has a ‘.MYI’ (MYIndex) extension, |
||||||||||||||||||||
| Q:64 | What is maximum size of a database in MySQL? | ||||||||||||||||||||
| A:64 | If the operating system or filesystem places a limit on the number of files in a directory, MySQL is bound by that constraint.The efficiency of the operating system in handling large numbers of files in a directory can place a practical limit on the number of tables in a database. If the time required to open a file in the directory increases significantly as the number of files increases, database performance can be adversely affected. The amount of available disk space limits the number of tables. MySQL 3.22 had a 4GB (4 gigabyte) limit on table size. With the MyISAM storage engine in MySQL 3.23, the maximum table size was increased to 65536 terabytes (2567 – 1 bytes). With this larger allowed table size, the maximum effective table size for MySQL databases is usually determined by operating system constraints on file sizes, not by MySQL internal limits.The InnoDB storage engine maintains InnoDB tables within a tablespace that can be created from several files. This allows a table to exceed the maximum individual file size. The tablespace can include raw disk partitions, which allows extremely large tables. The maximum tablespace size is 64TB. The following table lists some examples of operating system file-size limits. This is only a rough guide and is not intended to be definitive. For the most up-to-date information, be sure to check the documentation specific to your operating system. Operating System File-size LimitLinux 2.2-Intel 32-bit 2GB (LFS: 4GB) Linux 2.4+ (using ext3 filesystem) 4TB Solaris 9/10 16TB NetWare w/NSS filesystem 8TB Win32 w/ FAT/FAT32 2GB/4GB Win32 w/ NTFS 2TB (possibly larger) MacOS X w/ HFS+ 2TB |
||||||||||||||||||||
| Q:65 | Give the syntax of Grant and Revoke commands? | ||||||||||||||||||||
| A:65 | The generic syntax for grant is as following > GRANT [rights] on [database/s] TO [username@hostname] IDENTIFIED BY [password] now rights can be a) All privileges b) combination of create, drop, select, insert, update and delete etc.We can grant rights on all databse by using *.* or some specific database by database.* or a specific table by database.table_name username@hotsname can be either username@localhost, username@hostname and username@% where hostname is any valid hostname and % represents any name, the *.* any condition password is simply the password of userThe generic syntax for revoke is as following > REVOKE [rights] on [database/s] FROM [username@hostname] now rights can be as explained above a) All privileges b) combination of create, drop, select, insert, update and delete etc. username@hotsname can be either username@localhost, username@hostname and username@% where hostname is any valid hostname and % represents any name, the *.* any condition |
||||||||||||||||||||
| Q:66 | Explain Normalization concept? | ||||||||||||||||||||
| A:66 | The normalization process involves getting our data to conform to three progressive normal forms, and a higher level of normalization cannot be achieved until the previous levels have been achieved (there are actually five normal forms, but the last two are mainly academic and will not be discussed).First Normal FormThe First Normal Form (or 1NF) involves removal of redundant data from horizontal rows. We want to ensure that there is no duplication of data in a given row, and that every column stores the least amount of information possible (making the field atomic).Second Normal FormWhere the First Normal Form deals with redundancy of data across a horizontal row, Second Normal Form (or 2NF) deals with redundancy of data in vertical columns. As stated earlier, the normal forms are progressive, so to achieve Second Normal Form, your tables must already be in First Normal Form.Third Normal Form I have a confession to make; I do not often use Third Normal Form. In Third Normal Form we are looking for data in our tables that is not fully dependant on the primary key, but dependant on another value in the table |
||||||||||||||||||||
| Q:67 | How can we find the number of rows in a table using MySQL? | ||||||||||||||||||||
| A:67 | Use this for mysql >SELECT COUNT(*) FROM table_name; |
||||||||||||||||||||
| Q:68 | How can we find the number of rows in a result set using PHP? | ||||||||||||||||||||
| A:68 | $result = mysql_query($sql, $db_link); $num_rows = mysql_num_rows($result); echo "$num_rows rows found"; |
||||||||||||||||||||
| Q:69 | How many ways we can we find the current date using MySQL? | ||||||||||||||||||||
| A:69 | SELECT CURDATE(); CURRENT_DATE() = CURDATE() for time use SELECT CURTIME(); CURRENT_TIME() = CURTIME() |
||||||||||||||||||||
| Q:70 | What are the advantages and disadvantages of Cascading Style Sheets? |
||||||||||||||||||||
| A:70 | External Style SheetsAdvantagesCan control styles for multiple documents at once. Classes can be created for use on multiple HTML element types in many documents. Selector and grouping methods can be used to apply styles under complex contextsDisadvantagesAn extra download is required to import style information for each document The rendering of the document may be delayed until the external style sheet is loaded Becomes slightly unwieldy for small quantities of style definitionsEmbedded Style Sheets Advantages Classes can be created for use on multiple tag types in the document. Selector and grouping methods can be used to apply styles under complex contexts. No additional downloads necessary to receive style information Disadvantages This method can not control styles for multiple documents at once Inline Styles Advantages Useful for small quantities of style definitions. Can override other style specification methods at the local level so only exceptions need to be listed in conjunction with other style methods Disadvantages Does not distance style information from content (a main goal of SGML/HTML). Can not control styles for multiple documents at once. Author can not create or control classes of elements to control multiple element types within the document. Selector grouping methods can not be used to create complex element addressing scenarios |
||||||||||||||||||||
| Q:71 | What type of inheritance that PHP supports? | ||||||||||||||||||||
| A:71 | In PHP an extended class is always dependent on a single base class, that is, multiple inheritance is not supported. Classes are extended using the keyword ‘extends’. |
||||||||||||||||||||
| Q:72 | What is the difference between Primary Key and Unique key? |
||||||||||||||||||||
| A:72 | Primary Key: A column in a table whose values uniquely identify the rows in the table. A primary key value cannot be NULL. Unique Key: Unique Keys are used to uniquely identify each row in the table. There can be one and only one row for each unique key value. So NULL can be a unique key.There can be only one primary key for a table but there can be more than one unique for a table. |
||||||||||||||||||||
Q:73 |
The structure of table view buyers is as follows:
the following conditions? Condition1: Delete all the rows and insert another row then. What is the starting value for this auto incremented field user_pri_id , Condition2: Delete the last row(having the field value 999) and insert another row then. What is the value for this auto incremented field user_pri_id |
||||||||||||||||||||
| A:73 | In both cases let the value for auto increment field be n then next row will have value n+1 i.e. 1000 |
||||||||||||||||||||
| Q:74 | What are the advantages/disadvantages of MySQL and PHP? | ||||||||||||||||||||
| A:74 | Both of them are open source software (so free of cost), support cross platform. php is faster then ASP and JSP. |
||||||||||||||||||||
| Q:75 | What is the difference between GROUP BY and ORDER BY in Sql? | ||||||||||||||||||||
| A:75 | ORDER BY [col1],[col2],…,[coln]; Tels DBMS according to what columns it should sort the result. If two rows will hawe the same value in col1 it will try to sort them according to col2 and so on.GROUP BY [col1],[col2],…,[coln]; Tels DBMS to group results with same value of column col1. You can use COUNT(col1), SUM(col1), AVG(col1) with it, if you want to count all items in group, sum all values or view average |
||||||||||||||||||||
| Q:76 | What is the difference between char and varchar data types? | ||||||||||||||||||||
| A:76 | Set char to occupy n bytes and it will take n bytes even if u r storing a value of n-m bytes Set varchar to occupy n bytes and it will take only the required space and will not use the n bytes eg. name char(15) will waste 10 bytes if we store ‘mizan’, if each char takes a byte eg. name varchar(15) will just use 5 bytes if we store ‘mizan’, if each char takes a byte. rest 10 bytes will be free. |
||||||||||||||||||||
| Q:77 | What is the functionality of md5 function in PHP? | ||||||||||||||||||||
| A:77 | Calculate the md5 hash of a string. The hash is a 32-character hexadecimal number. I use it to generate keys which I use to identify users etc. If I add random no techniques to it the md5 generated now will be totally different for the same string I am using. |
||||||||||||||||||||
| Q:78 | How can I load data from a text file into a table? | ||||||||||||||||||||
| A:78 | you can use LOAD DATA INFILE file_name; syntax to load data from a text file. but you have to make sure thata) data is delimited b) columns and data matched correctly |
||||||||||||||||||||
| Q:79 | How can we know the number of days between two given dates using MySQL? |
||||||||||||||||||||
| A:79 | SELECT DATEDIFF(’2007-03-07′,’2005-01-01′); | ||||||||||||||||||||
| Q:80 | How can we know the number of days between two given dates using PHP? |
||||||||||||||||||||
| A:80 | $date1 = date(‘Y-m-d’); $date2 = ’2006-08-15′; $days = (strtotime($date1) – strtotime($date2)) / (60 * 60 * 24); |
| Q:81 | What is ‘float’ property in CSS? |
| A:81 | The float property sets where an image or a text will appear in another element. |
| Q:82 | What is descendant structure in CSS? |
| A:82 | Descendant selectors are used to select elements that are descendants of another element in the document tree.For example, you may wish to target a specific <em> element on the page, but not all <em> elements. A sample document could contain the following code: <body> <h1>Heading <em>here</em> </h1> <p>Lorem ipsum dolor <em>sit</em> amet.</p> </body> The document tree diagram (with the <em> element to be targeted) would be: em {color: blue; } However, if you use a descendant selector, you can refine the <em> elements that you select. The rule below will only select <em> elements that are descendants of <p> elements. If this rule is applied, the <em> element within the <h1> will not be colored blue. p em {color: blue; } You can also jump levels in the document tree structure to select descendants. For example, the following code: <body> <p>Lorem ipsum dolor <em>sit</em> amet.</p> <ul> <li>item 1</li> <li>item 2</li> <li><em>item 3</em></li> </ul> </body> The document tree (with a third-level <em> element highlighted) would be: Using the following rule you can isolate any <em> element inside a <ul> element, without having to describe the <li> element. If this rule is applied, any <em> element within a <ul> element will be colored blue. However, the <em> element within the <p> will not be colored blue: ul em {color: blue; } Descendant selectors are well supported across standards-compliant browsers. |
| Q:83 | What is Child Descendant structure in CSS? |
| A:83 | Child selectorsA child selector is used to select an element that is a direct child of another element (parent). Child selectors will not select all descendants, only direct children.For example, you may wish to target an <em> that is a direct child of a <div>, but not other <em> elements that are descendants of the <div>. A sample document could contain the following code: <body> <h1>Heading <em>text</em></h1> <div> This is some <em>text</em> <p>This is a paragraph of <em>text</em></p> </div> </body> The document tree (highlighting the <em> that is a child of the <div>) would be: Using the following rule you can target any <em> element that is a child of the <div>. Other <em> elements that are descendants but not direct children of the <div> will not be targeted. div > em { color: blue; } OR div>em { color: blue; } Child selectors are not supported by Windows Internet Explorer 5, 5.5 and 6, but are supported by most other standards-compliant browsers. |
| Q:84 | How to create a class in JavaScript? |
| A:84 | Classes can seem off-putting at first, but once you see the point of them, their use can be invaluable.We have already met objects. A computer object is a representation of a real object. For an estate agent the object may be a house, including information about the number of rooms and the price.An estate agent may have a lot of houses available. These houses all have different characteristics, and as objects they all go through the same processes. They are viewed, surveyed and bought, and so on.A full estate agent program would be difficult to demonstrate here, but we can introduce the use of classes.In this example, we have the house class. The house class produces house objects, all with object properties, such as number of rooms and price, and all having access to the same methods, such as sold and bought.
So a class can create objects with a group of properties and methods. JavaScript doesn’t have a keyword specific to class, so we must go back to basics and develop classes in a different way. This isn’t very difficult. Class PropertiesLet us examine a very small estate agent program.<HTML> <HEAD> <TITLE>Estate Agent</TITLE> <SCRIPT> function House(rooms,price,garage) { this.rooms=rooms; this.price=price; this.garage=garage; } house1=new House(4,100000,false); house2=new House(5,200000,true); with (house1) document.write(‘House 1 has ‘+rooms+’ rooms, ‘+(garage?’a':’no’)+’ garage, and costs £’+price+’<BR>’); with (house2) document.write(‘House 2 has ‘+rooms+’ rooms, ‘+(garage?’a':’no’)+’ garage, and costs £’+price+’<BR>’); </SCRIPT> </HEAD> </HTML> We define a House function that takes three parameters, rooms, price and garage. The function uses the this keyword to create an object. When we call the House function, we assign the result to our variable, which becomes an object. So, identical code would be: house1=new Object(); house1.rooms=4; house1.price=100000; house1.garage=false; We would have to type this in for all houses, which would be very tedious and is why we use the class structure instead. When we display the details for a house, I have introduced the ternary operator, ‘?:’. The ternary operator is a compacted version of: if (garage) str=’a'; else str=’no’; (garage?’a':’no’) means if garage is true, return ‘a’ else return ‘no’. Using the ternary operator removes a line of code, and avoids having to create a new variable. Class MethodsThe House class we have so far defined only contains object properties. We could add a method to replace the document.write() action we used before. (See example)<HTML> <HEAD> <TITLE>Estate Agent 2</TITLE> <SCRIPT> function House(name,rooms,price,garage) { this.name=name; this.rooms=rooms; this.price=price; this.garage=garage; this.view=view; } function view() { with (this) document.write(name+’ has ‘+rooms+’ rooms, ‘+(garage?’a':’no’)+’ garage, and costs £’+price+’<BR>’); } house1=new House(‘House 1′,4,100000,false); house2=new House(‘Big House’,5,200000,true); house1.view(); house2.view(); </SCRIPT> </HEAD> </HTML> Much better! Note how we must add another property, name, so that we can identify the house in question. This offers more flexibility than re-using the variable name, and the variable name is inaccessible anyway, i.e. it is very difficult, if not impossible, to get the view() function to use the string ‘house1′. |
| Q:85 | Are namespaces are there in JavaScript? |
| A:81 | A namespace is a container and allows you to bundle up all your functionality using a unique name. In JavaScript, a namespace is really just an object that you’ve attached all further methods, properties and objects. But it is not always necessary to use namespace. |
| Q:86 | What is JSON? What are the notations used in JSON? |
| A:86 | JSON (JavaScript Object Notation) is a lightweight data-interchange format. It is easy for humans to read and write. It is easy for machines to parse and generate. It is based on a subset of the JavaScript Programming Language, Standard ECMA-262 3rd Edition – December 1999. JSON is a text format that is completely language independent but uses conventions that are familiar to programmers of the C-family of languages, including C, C++, C#, Java, JavaScript, Perl, Python, and many others. These properties make JSON an ideal data-interchange language. |
| Q:87 | How to get Query String in PHP for http request? |
| A:87 | $_GET[] and $_REQUEST[] |
| Q:88 | How to get the http Request in PHP? |
| A:88 | When PHP is used on a Web server to handle a HTTP request, it converts information submitted in the HTTP request as predefined variables:
|
| Q:89 | How you provide security for PHP application? |
| A:89 | There are many ways to accomplish the security tasks but the most common 7 ways are1. Validate Input. Never trust your user and always filter input before taking it to any operation.2. Provide access control.3. Session ID protection4. preventing Cross Site Scripting (XSS) flaws
5. SQL injection vulnerabilities. 6. Turning off error reporting and exposing to the site for hackers. Instead use log file to catch exceptions 7. Effective Data handling |
| Q:90 | What is SQL Injection in PHP security? |
| A:90 | SQL injection attacks are extremely simple to defend against, but many applications are still vulnerable. Consider the following SQL statement:
<?php $sql = "INSERT INTO users (reg_username, reg_password, reg_email) VALUES ('{$_POST['reg_username']}', '$reg_password', '{$_POST['reg_email']}')"; ?>
This query is constructed with $_POST, which should immediately look suspicious.Assume that this query is creating a new account. The user provides a desired username and an email address. The registration application generates a temporary password and emails it to the user to verify the email address. Imagine that the user enters the following as a username: bad_guy', 'mypass', ''), ('good_guy
This certainly doesn’t look like a valid username, but with no data filtering in place, the application can’t tell. If a valid email address is given (shiflett@php.net, for example), and 1234 is what the application generates for the password, the SQL statement becomes the following:<?php $sql = "INSERT INTO users (reg_username, reg_password, reg_email) VALUES ('bad_guy', 'mypass', ''), ('good_guy', '1234', 'shiflett@php.net')"; ?>
Rather than the intended action of creating a single account (good_guy) with a valid email address, the application has been tricked into creating two accounts, and the user supplied every detail of the bad_guy account.While this particular example might not seem so harmful, it should be clear that worse things could happen once an attacker can make modifications to your SQL statements. For example, depending on the database you are using, it might be possible to send multiple queries to the database server in a single call. Thus, a user can potentially terminate the existing query with a semicolon and follow this with a query of the user’s choosing. MySQL, until recently, does not allow multiple queries, so this particular risk is mitigated. Newer versions of MySQL allow multiple queries, but the corresponding PHP extension (ext/mysqli) requires that you use a separate function if you want to send multiple queries (mysqli_multi_query() instead of mysqli_query()). Only allowing a single query is safer, because it limits what an attacker can potentially do. Protecting against SQL injection is easy:
|
| Q:91 | What is cross site Scripting? |
| A:91 | To understand what Cross Site Scripting is, let’s see a usual situation, common to many sites. Let’s say we are taking some information passed in on a querystring (the string after the (?) character within a URL), with the purpose of displaying the content of a variable, for example, the visitor’s name: http://www.yourdomain.com/welcomedir/welcomepage.php?name=John As we can see in this simple querystring, we are passing the visitor’s name as a parameter in the URL, and then displaying it on our “welcomepage.php” page with the following PHP code: <?php echo ‘Welcome to our site ’ . stripslashes($_GET[‘name’]); ?> The result of this snippet is shown below: Welcome to our site John This is pretty simple and straightforward. We’re displaying the content of the “name” variable, by using the $_GET superglobal PHP array, as we have done probably hundreds of times. Everything seems to be fine. Now, what’s wrong with this code? Nothing really. But let’s modify the querystring by replacing our visitor’s name passed in the URL: http://www.yourdomain.com/welcomedir/ welcomepage.php?name=John with something like this: http://www.yourdomain.com/welcomedir/ welcomepage.php?name= <script language=javascript>alert (‘Hey, you are going to be hijacked!’);</script> Do you remember the PHP code included in our “welcome.php” page? Yes, you’re correct. When we modify the querystring, the following code is executed: <?php echo ‘Welcome to our site ‘ . <script language=javascript> alert(‘Hey, you are going to be hijacked!’);</script> ?> The output of this code is an alert JavaScript box telling you “Hey, you are going be hijacked!” after the “Welcome to our site” phrase. Very ugly stuff, right? That’s a simple example of the Cross Site Scripting vulnerability. This means that any pasted JavaScript code into the URL will be executed happily with no complaints at all. |
| Q:92 | Which method do you follow to get a record from a million records? (Searching, …. not from database, from an array in php) |
| A:92 | use array_search(), array_keys(), array_values(), array_key_exists(), and in_array(). |
What is difference between final and static?
ReplyDeleteWhenvere you declare a variable as static,then the static variable will have a single copy that is shared by all the objects. so any modifications to the static
variable will modify it's value in all objects.
And we can access static varibale directly by using class name
Example : ClassName.VariableName.:
Whenvere we decalre varibal as a final,then the variable cannot be changeable during the execution of the program.
the ``final'' keyword, when applied to a variable, means the variable's value is constant.
eg. final int RED = 1;
The ``final'' keyword is useful when applied to variables whose values will not change during the lifetime of the program.
The keyword ``static'' when applied to a variable OR a method means that the variable or method can be accessed without creating an instance of the class.
When ``final'' is applied to a class, the principle effect is that the class cannot be inherited from.
static means the reference is constant whereas final means the value is constant
What is the difference between MyIsam and InnoDB?
ReplyDeleteThe big difference between MySQL Table Type MyISAM and InnoDB is that InnoDB supports transaction
InnoDB supports some newer features: Transactions, row-level locking, foreign keys
InnoDB is for high volume, high performance
Most people use MyISAM if they need speed and InnoDB for data integrity.
InnoDB has been designed for maximum performance when processing large data volumes.
How do you display sum of salaries in a organisation?
ReplyDeletesuppose emp(eid,name,did) dept(did,dname,salary)
select d.dname,sum(salary) from emp e
inner join dept d on d.did=e.did group by e.did
What are different ways to declare constructor in PHP?
ReplyDelete1.
<?php
class BaseClass {
function __construct() {
print "In BaseClass constructor\n";
}
}
?>
2.
<?php
namespace Foo;
class Bar {
public function Bar() {
// treated as constructor in PHP 5.3.0-5.3.2
// treated as regular method as of PHP 5.3.3
}
}
?>
Can we access 'static' method using class object?
ReplyDeleteDeclaring class properties or methods as static makes them accessible without needing an instantiation of the class. A property declared as static can not be accessed with an instantiated class object.
Because static methods are callable without an instance of the object created, the pseudo-variable $this is not available inside the method declared as static.
Static properties cannot be accessed through the object using the arrow operator ->.
Calling non-static methods statically generates an E_STRICT level warning.
Like any other PHP static variable, static properties may only be initialized using a literal or constant; expressions are not allowed. So while you may initialize a static property to an integer or array (for instance), you may not initialize it to another variable, to a function return value, or to an object.
Can we extend more than one class in PHP?
ReplyDeleteA class can inherit the methods and properties of another class by using the keyword extends in the class declaration. It is not possible to extend multiple classes; a class can only inherit from one base class.
The inherited methods and properties can be overridden by redeclaring them with the same name defined in the parent class. However, if the parent class has defined a method as final, that method may not be overridden.
What are 'properties' of a class?
ReplyDeleteClass member variables are called "properties". You may also see them referred to using other terms such as "attributes" or "fields".
In order to maintain backward compatibility with PHP 4, PHP 5 will still accept the use of the keyword var in property declarations instead of (or in addition to) public, protected, or private. However, var is no longer required. In versions of PHP from 5.0 to 5.1.3, the use of var was considered deprecated and would issue an E_STRICT warning, but since PHP 5.1.3 it is no longer deprecated and does not issue the warning.
If you declare a property using var instead of one of public, protected, or private, then PHP 5 will treat the property as if it had been declared as public.
What are different visibility of a property or method?
ReplyDeletepublic: can be accessed everywhere.
protected: can be accessed only within the class itself and by inherited and parent classes.
private: may only be accessed by the class that defines the member.
What are keywords used to access properties ore methods inside the class?
ReplyDeleteThree special keywords self, parent and static are used to access properties or methods from inside the class definition.
What are abstract classes?
ReplyDeleteClasses defined as abstract may not be instantiated, and any class that contains at least one abstract method must also be abstract. Methods defined as abstract simply declare the method's signature - they cannot define the implementation.
When inheriting from an abstract class, all methods marked abstract in the parent's class declaration must be defined by the child; additionally, these methods must be defined with the same (or a less restricted) visibility.
the signatures of the methods must match, i.e. the type hints and the number of required arguments must be the same.
Explain about Interfaces?
ReplyDeleteInterfaces are defined using the interface keyword, in the same way as a standard class, but without any of the methods having their contents defined.
All methods declared in an interface must be public, this is the nature of an interface.
To implement an interface, the implements operator is used.
All methods in the interface must be implemented within a class; failure to do so will result in a fatal error.
Classes may implement more than one interface if desired by separating each interface with a comma.
What are difference between abstract class and interface?
ReplyDelete1
Abstract: For abstract class a method must be declared as abstract. Abstract methods doesn’t have any implementation.
Interface: For interface all the methods by default are abstract methods only. So one cannot declare variables or concrete methods in interfaces.
2
Abstract: The Abstract methods can declare with Access modifiers like public, internal, protected. When implementing in subclass these methods must be defined with the same (or a less restricted) visibility.
Interface: All methods declared in an interface must be public.
3
Abstract: Abstract class can contain variables and concrete methods.
Interface: Interfaces cannot contain variables and concrete methods except constants.
4
Abstract: A class can Inherit only one Abstract class and Multiple inheritance is not possible for Abstract class.
Interface: A class can implement many interfaces and Multiple interface inheritance is possible.
How do we exchange two varaibles without using temporary variable?
ReplyDeleteAns:list($a,$b) = array($b,$a);
Write a query to find out 4th hieghest marks getter from the below table
ReplyDeleteName English,Maths,Statistics
John 80,70,77
Adi 90,65,85
Vasu 56,36,89
Prasanth 36,85,65
Sujala 89,65,36
Ans:
select *,(English+Maths+Statistics) as tot from mark order by tot desc limit 3,1
Write a custom function which gives complete text without breaking work after specifying n as limit. Example:'Adiyya lives simple living' 10 is limit it should give 'Adiyya lives' rather than 'Adiyya liv'
ReplyDeleteAns:
function safeSplit($str,$n)
{
if($str[$n] != ' ')
{
$part = substr($str,$n);
$parts = explode(' ',$part);
$returnString = substr($str,0,$n).$parts[0];
}
else
$returnString = substr($str,0,($n-1));
return $returnString;
}
echo safeSplit('Adiyya lives simple life',10);
Write a custom function to find all pairs of integers within an array which sum to a specified value, For example if the value is 5 and array is {4,1,3,1,2,4,1} answer should be {4,1},{3,2}. Remember there should not be any repetion like {4,1},{4,1}. Note:Please do not use any build in PHP functions except count.
ReplyDeleteAns:
function arrayCheck($needle, $heyStack)
{
for ($i = 0; $i < count($heyStack); $i++)
{
if($heyStack[$i] == $needle)
{
return true;
}
}
return false;
}
function pairSum( $array, $sum )
{
$uniqueNumbersArray = array();
$pairsArray = array();
if(count($array) > 0)
{
for($i = 0; $i < count($array); $i++)
{
if(!arrayCheck($array[$i],$uniqueNumbersArray))
$uniqueNumbersArray[] = $array[$i];
}
for($i = 0; $i < count( $uniqueNumbersArray ); $i++)
{
for($k = 0; $k < count( $uniqueNumbersArray ); $k++)
{
$sumTemp = $uniqueNumbersArray[$i]+$uniqueNumbersArray[$k];
if( $sumTemp == $sum )
$pairsArray[] = '{'.$uniqueNumbersArray[$i].','.$uniqueNumbersArray[$k].'}';
}
}
return $pairsArray;
}
}
$findArray = array(4,1,3,1,2,4,1);
print_r(pairSum($findArray,4));